Where do I start?
Are you looking to write a cybersecurity incident response plan but have no idea where to start? You’ve come to the right place! Let’s review some tips for establishing a robust cybersecurity incident response plan.
Why We’re Here
In many of my previous Cybersecurity-based articles, I noted that cybersecurity is a big, scary, and fairly new topic. Sure, people talked about cybersecurity 20 years ago. But the businesses of that era weren’t dealing with the frequency of attacks, or exposure, that modern businesses are.
If you’re running a profitable business just assume that you’re a target for cybercrime. If you’re a startup with a digital marketing strategy that’s successful, assume that you’re a target. Visibility is critical to the marketing success of your company. Meanwhile, it also makes the digital world aware that your business exists. And just like in the physical world, there are some serious jerks in the digital world. Unfortunately, some of them are really good at exploiting people and extorting businesses.

Cybersecurity breaches happen. That is to say, there is no such thing as a business or organization that is impervious to cyber threats. What makes businesses resilient is how they prepare and how they respond. It’s best to block an attack altogether. However, knowing how to respond during a cyber attack is just as important.
Write Out A Rough Cybersecurity Incident Response Plan
To start, let’s not get tripped up on outlining all the content that should be included. Ignore what the best document template is for now. All of that can come later. You need to start writing this thing out. Any blank text document is a good place to start.
Your initial draft isn’t going to be great. It doesn’t have to be. Our focus needs to be on documenting what needs to be addressed. You just need a general response plan that covers its fair share of bases. You can then use it as a template for creating documents for individual scenarios.
Don’t write this document to cover every single fringe case you can think up. The document will become too complex, long, and hard to use. And if it’s not used, there was no point in writing it.
Personally, I like to start with What, Who, then How.
What
We’re writing an incident response plan. But for what? Phishing Scams? Ransomware attacks? Data Theft? Yes. In general, these are the three most common types of attacks that businesses face. That is because most modern cyber attacks on businesses are for monetary reasons. Threat actors are trying to extort you. Data and money are valuable assets. With that in mind, Phishing Scams, Ransomware Attacks, and Data Theft should be the general focus.
There are other types of attacks that are not for monetary purposes, or specific to businesses. For example, malware can be used to extort businesses. It’s also commonly used to target and disrupt individuals as well.
Malware is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive users access to information or which unknowingly interferes with the user’s computer security and privacy.
Wikipedia
Adware is similar in nature. Websites for some industries are prone to DDoS attacks. If you deal with specific types of attacks routinely they should be addressed as a What. You may want to take some time and research what types of attacks businesses in your industry are prone to.
Now that you know what you are responding to you can determine Who in your organization will respond.
Who
IT is responsible for all of this. Done.

Kidding. Although that’s pretty much how most businesses feel about cybersecurity response. However, there may be actions that need to be taken that employees in other departments are best suited for.
For example, if your response team isolates a breach and finds out the location, user, and computer that was used to cause it, you want that computer off the network ASAP. If you don’t have a network switch that can be remotely monitored or managed, you need someone to physically unplug the network cable from the device, or even better shut the device down. Some ransomware is fairly sophisticated. They can block attempts at remote management by your IT service provider or in-house IT.
In this scenario, I would identify a point of contact (based on the employee’s position) for each of your physical locations that can be contacted to physically access a computer. If you’re in an industry with high turn-around, identify a backup position that would be responsible for this task.
Yes, IT is ultimately responsible for incident response. And yes, they should have their own process of identifying Who needs to be involved with What.
However, consider that they also need support from employees in other departments.
How
It’s easy to get caught up in the actions needed to patch a vulnerability and respond to an attack. However, the communication around an incident is just as important. Properly reporting and escalating an incident prevents those that need to be involved from being blindsided. It also keeps those who don’t need to be involved out of the picture and out of your hair while you are responding.
Would you rather be briefed Monday morning or receive a call from a Systems Administrator Saturday morning when the breach occurs? Is someone else better equipped to respond? Don’t assume that your employees know the answer to these questions. State it clearly in your plan.

Communication aside, you don’t want to be too extreme with your response to each type of threat. That can kill productivity. You’ll need to…
Measure the response to the Threat
I can tell you from personal experience as the responsible party that a cybersecurity breach gets your blood flowing. It’s stressful and you go into it feeling like you’ve already failed. It’s easy to overreact to an incident out of an abundance of caution.
It’s also a huge waste of time and resources.
For example, a successful Phishing Scam that gets credit card information from one of your finance employees doesn’t require a full lockdown of all finance employees and their technology. It requires that you call the bank, review any fraudulent charges, and deactivate the card. After that, you also need to alert IT immediately so they can analyze the email, text, or platform used to execute the scam for further vulnerability.
Severity
Some breaches are really low-level and don’t require a huge reaction. When it comes to writing an incident response plan, it helps to have some framework for the severity of the incident. Something as simple as Low, Medium, High is enough. Let’s look at a very simple severity scale used by IT departments for the prioritization of incoming tickets:
- Low – Impacting only a single user
- Medium – Impacting a group of users
- High – Impacting the entire company
Cybersecurity response is a bit different than operating an IT help desk, but this is a nice baseline. In addition to the operational impact, there are incident-specific concerns that should be addressed as well.
The monetary impact should be considered in the severity of incidents involving extortion, like ransomware. For incidents involving data theft, you may need to engage a 3rd party Public Relations firm to handle communications. If your customer’s personal information was stolen and/or leaked you are obligated to make a public announcement. How you word that communication can be a very delicate matter, and hurt your business reputation if not handled correctly. Having the guidance of a PR firm really helps in these situations.
When writing an incident response plan, make sure that each type of incident has a scale that makes sense and is clear enough to be acted on.
Security Training
Every incident should be followed up with a training session. It’s easy for this step to get lost in the day-to-day operations of a business, but if you don’t train the employees the incident will happen again. Closing out the incident alone is not enough.
Business email compromise cost $1.7 Billion in 2021
33% of breaches were preventable phishing scams
Businesses with routine training and phishing simulations reduced their click through rate by 65%
Webroot 2021
Wait… you’re not a cybersecurity expert, but you’re going to train your employees on the subject? Doesn’t add up. The good news is there are plenty of systems out there that can safely simulate cybersecurity attacks, log who fell for it, and curate training videos, articles, and quizzes for the offending user to use for training.
For example, IT Ninjas uses IronScales as its go-to enhanced email security platform. IronScales has phishing simulations and training built right into the system. It also includes a reporting and tracking platform so you can review how well your team is performing on their assessments.
Follow the Plan
Each time you encounter one of these attacks you should see it as a chance to refine your response to it. The image below shows the cycle you should be using to refine your documentation and improve your business response over time.
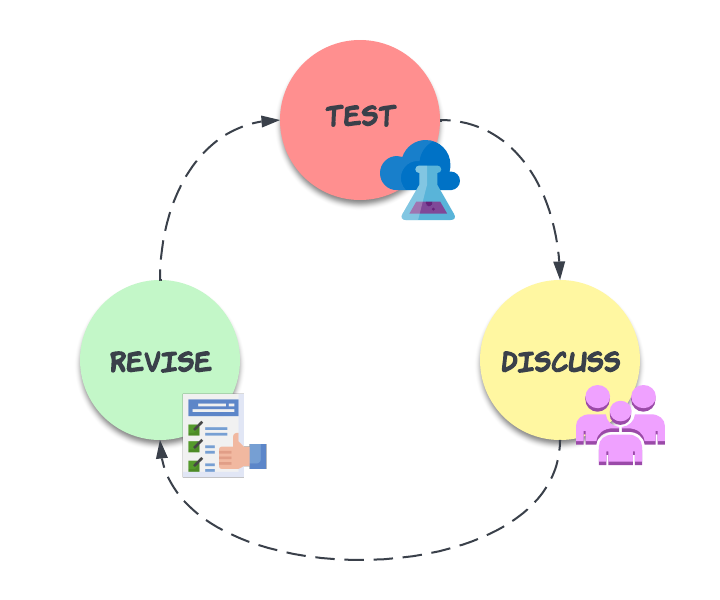
Test the Documentation
This is pretty simple. Instead of running in blind and trying to be a hero when an incident occurs, stop, take a deep breath, and grab your Incident Response Plan document. Now follow it 100% where possible. If the plan does not account for a specific circumstance, note it. Once the incident is resolved it’s time to discuss it with your team.
Discuss Cybersecurity Response Plan with Team
Hold a meeting with your team and discuss the incident. These meetings are also known as a postmortem, or debrief. Now that the incident is over, you can meet with the team and compare notes. Did the plan account for everything? Was one of your noted deficiencies likely to impact the business again in the future? Or was it just a fringe case?
A word to the wise: you may want to wait 24-48 hours after the incident to sit everyone down together. This will allow the team to decompress. You want to avoid this devolving into a room full of people finger-pointing. I’ve been there. After some incidents you’re dealing with a group of high-strung technicians coming down off of a stressful 16-hour shift and several gallons of coffee. It’s probably a good idea to have that meeting after everyone has had a chance to cool down.
Revise the Documentation
You’ve all agreed upon the changes, now it’s time to apply them to the document.
Test the Documentation
You are officially ready to go attack the next incident with fresh documentation. Repeat this loop with your team as often as possible. If you notice that your documentation is getting too long or too complex, it’s time to start breaking out scenarios into individual documents.
Final Thoughts and Considerations
Now that you have a rough plan in place, you may also want to consider how to handle training and discipline. What happens to repeat offenders? How many free passes does an employee get in good faith?
Make sure you implement a monitoring period after the incident has been resolved. It is incredibly helpful. You want to make sure the threat doesn’t crop back up immediately and send you back to square 1.
Thank you for taking the time to read this, I hope it helped make your business more resilient to cyber-attacks. Best of luck developing your response plan! If you would like a free assessment of your business’s cybersecurity, reach out to us today!